Managed Security Services
Robust security monitoring & faster response to threats.
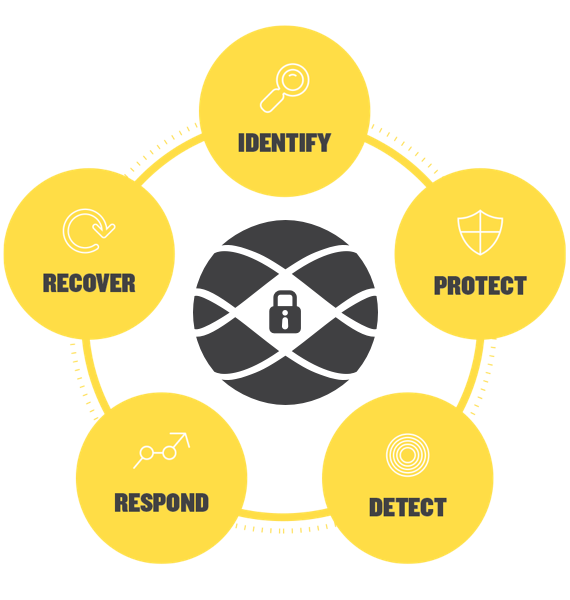
Automated and intelligent detection and response
Our goal is to provide complete cyber threat detection and response. Our people and systems provide contextualised threat analysis and rapid response to malicious threats as they arise in our customers' environment.
In today’s dynamic and evolving threat environment, internal security teams don’t have the time or resources to analyse emerging threats. That’s where customers can trust Kordia’s Security Operations Centre (SOC) to deliver managed security services.

Managed Security Services
Market-leading, highly experienced cyber security expertise, delivered as an end-to-end service - providing on-going guidance, support and protection of your most important assets.
Together we are stronger
With one of the largest cyber security teams in New Zealand who act as an extension to your own team, we have all the expertise you need to provide a unified approach to security.
Around the clock protection
Kordia’s 24/7, 365 managed security services and best in class technology can integrate with a host of other security services, providing you complete oversight and management of your security and network environment.
Tailored Results & Insights
We align our industry knowledge and expertise to your priorities. With dedicated research we continually evolve our managed security services ensuring best practice is applied at all times - giving you peace of mind and continued assurance.
Introducing Kordia's Security Operation Centre (SOC)
Kordia's SOC works as an extension of a businesses security team providing them with a level of assurance that frees them up to focus on other operations.

